About this Report
This report was created on KringleCraft.com, /ˈkrɪŋ.ɡəl krɑːft ˈkɑːm/. An online CTF solution editor and report generator inspired by SANS Holiday Hack Challenge & KringleCon.
Makes creating solutions and reports easy and fun 😀


About 2021 SANS Holiday Hack Challenge
KringleCon 4: Calling Birds!
About the Author Ben Krüger
I’m a Cyber Security Fanatic & Generic IT Fairy. I love doing riddles and solving problems. I have specialized in the area of cyber security but I’m far away from being an expert. I guess my average day is missing 8 additional hours, I do have a lovely family which is always number one! What’s left of the day I use to discover new things, try out software or even play CTF like stuff.
Report Summary and Notes
- FrostFest FrostTowerGiftShop
- FrostFest FrostTowerLobby
- FrostFest FrostTowerRooftop
- FrostFest JacksOffice
- FrostFest JacksRestroom
- FrostFest JacksStudio
- FrostFest TalksLobby
- FrostFest TheThirdKind
- KringleCon Courtyard
- KringleCon DiningRoom
- KringleCon Entry
- KringleCon GreatRoom
- KringleCon Kitchen
- KringleCon NetWars
- KringleCon SantasOffice
- KringleCon SpeakerUNpreparationRoom
- KringleCon TalksLobby
- TheNorthPole Orientation
- TheNorthPole TheNorthPole
- Objective 11 Customer Complaint Analysis
- Objective 4 Slot Machine Investiation
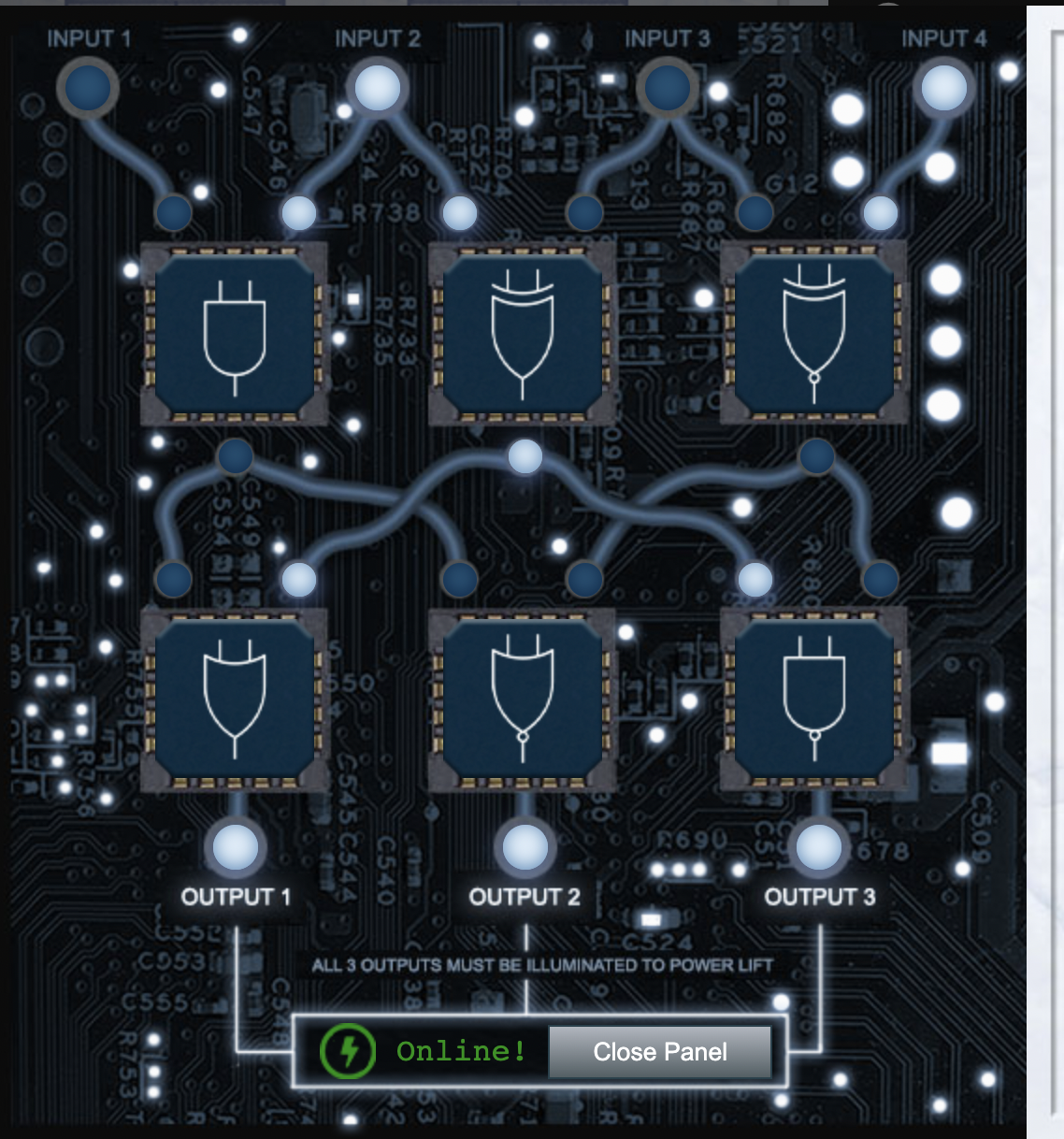
- Objective 13 FPGA Programming
- Objective 6 Shellcode Primer
- Objective 7 Printer Exploitation
- Objective 12 Frost Tower Website Checkup
- Objective 10 Now Hiring
- Objective 2 Where in the World is Caramel Santiago
- Objective 9 Splunk
- Objective 8 Kerberoasting on an Open Fire
- Objective 5 Strange USB Device
- Objective 1
- Objective 3